Who are the cyber criminals? Domestic online terrorists? The USG?
Check out CISA, the federal Cybersecurity and Infrastructure Security Agency within the Department of Homeland Security
https://edition.cnn.com/2023/06/15/politics/us-government-hit-cybeattack/index.html
Several US federal government agencies have been hit in a global cyberattack by Russian cybercriminals that exploits a vulnerability in widely used software, according to a top US cybersecurity agency.
https://www.theepochtimes.com/us-government-hit-in-global-hacking-campaign_5336379.html
Eric
Goldstein, the executive assistant director for cybersecurity at the
U.S. Cybersecurity and Infrastructure Security Agency (CISA), said in a
statement that several federal agencies had been compromised after the discovery of a vulnerability in the file transfer software MOVEit.CISA
did not identify the affected agencies or specify how they were
affected. It did not respond promptly to requests for additional
comment.Progress Software Corp’s (PRGS.O) MOVEit is
typically utilized by businesses to transmit files between partners and
customers. Progress stock declined by 4%.The online
extortion group Cl0p, which has claimed responsibility for the MOVEit
breach, has stated in the past that it would not use any data stolen
from government agencies.The group wrote that government agencies, cities, and police services shouldn’t worry because they had already erased the data.
https://www.rt.com/news/578105-us-government-agencies-cyberattack/
The US Cybersecurity and Infrastructure Security Agency “is providing support to several federal agencies that have experienced intrusions,” an agency official told the American broadcaster. “We are working urgently to understand impacts and ensure timely remediation.”
A
White Hat/Black hat “online extortion group” that breaks into
government databases but only steals from the private sector? Hmmm,
that sounds more like a government-rewarded hacking group to me. Or
maybe a cyber group within the USG.
It also sounds like they broke
into a LOT of different places. Now here is something you may not
know. Companies pay hackers large bounties to discover vulnerabilities.
And hackers can use that excuse to justify breaking into a system, if
caught. So hackers are constantly trying and finding ways to break into
computer systems.
https://www.pcmag.com/news/7-huge-bug-bounty-payouts
Bug bounties have become so commonplace that third-party brokers like Bugcrowd and HackerOne exist to connect hackers with bounty money. As detailed in HackerOne’s 2018 Hacker Report, the company has paid out over $23 million to the 166,000 hackers in its network alone, who have fixed over 72,000 vulnerabilities. That’s a lot of good work—for a lot less money than a true hack can cost a company in money and reputation.
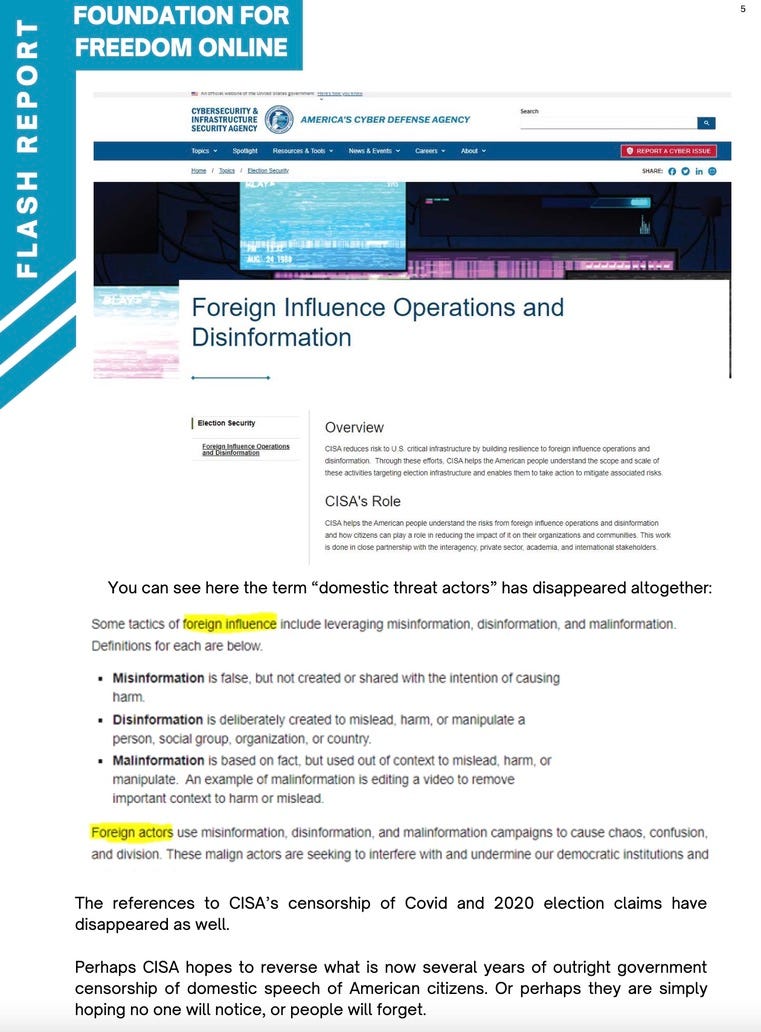
The
Cybersecurity and Infrastructure Security Agency has been in hot water
recently. It has been doing its best to erase its tracks after calling
us domestic terrorists for simply using our First Amendment right to
communicate and speak. The Foundation for Freedom Online, whose praises
I have repeatedly sung, tells us more about the not so subtle erasures
of what CISA has been up to. They are desperate to hang onto their new
terminology of “Misinformation, disinformation and malinformation” but
had to shut down their unit of the same name because it was illegally
spying on and censoring Americans. So now they have decided to blame
foreigners instead of domestic US persons—at leasst in public. This is
almost certainly a result of the Missouri v Biden discovery (and the
Twitter files’ deep dive) into only a fraction of what the USG agencies
were doing to silence any dissent.
https://foundationforfreedomonline.com/wp-content/uploads/2023/03/FFO-FLASH-REPORT-REV.pdf
There is lots more about this subject at the Foundation for Freedom online here.
More later on the crimes of the USG cyber villains. And go look at the Foundation for Freedom Online website with all it has to offer. It is a goldmine.